Introduction
The term "cross origin sharing" refers to the method that enables a page's limited resources to be requested from a domain other than the domain from which the first resource was supplied.
Cross-origin request:
CORS is a browser-implemented security mechanism that restricts browser access to external websites. A cross-origin request comes from a resource that is not part of the origin. A specification called CORS controls cross-origin requests.
A more simplistic explanation would be: Think of it like a security guard who keeps your family safe by preventing unauthorized individuals from entering your property.
Need for CORS
Web browsers use a security feature called same-origin policy to stop websites from interfering with one another. When it is desirable to use cross-domain scripting. The same-origin policy can be circumvented by web developers thanks to cross-origin resource sharing, or CORS.
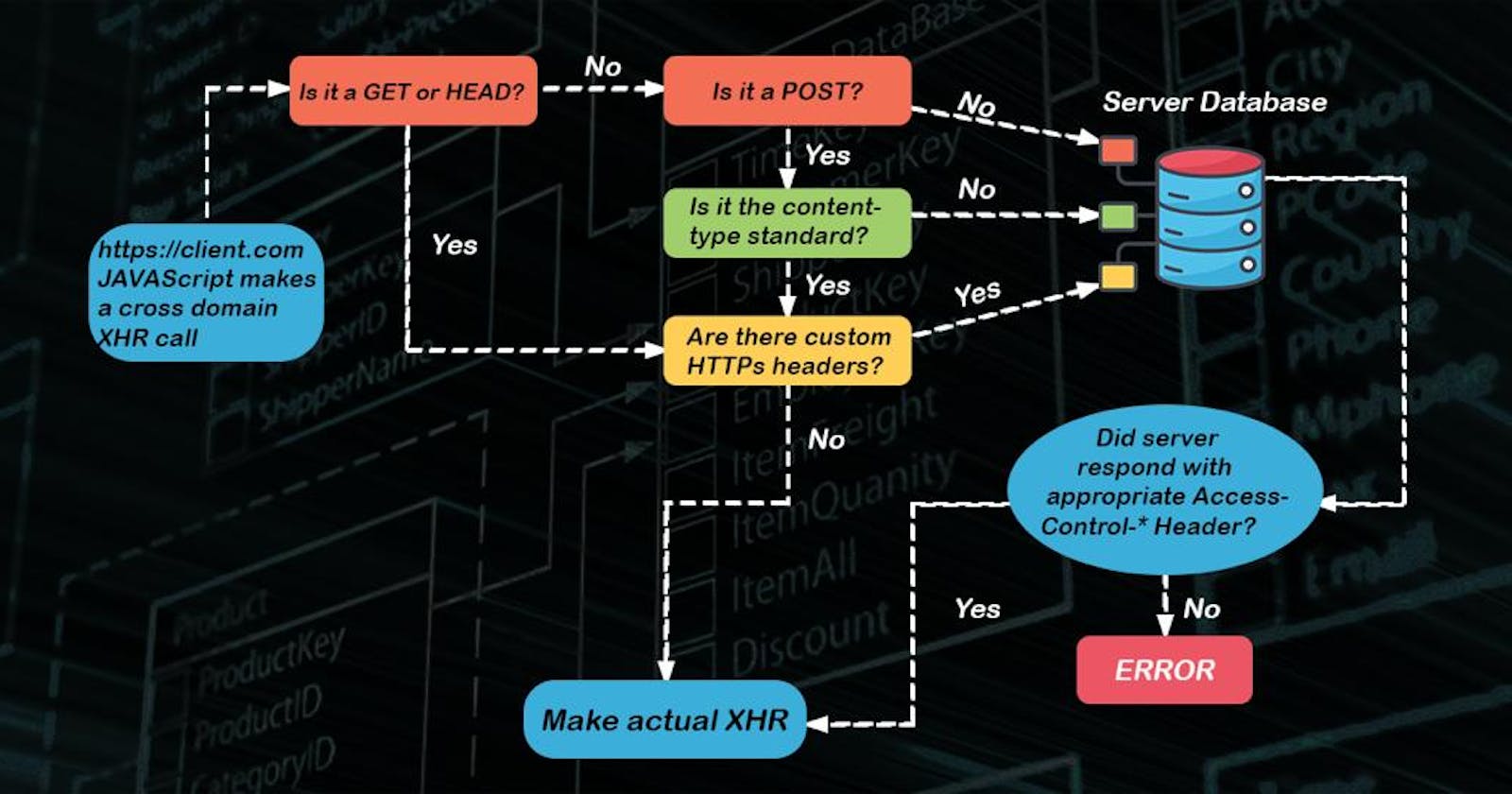
How does CORS work?
The same-origin policy, which is the default behavior in browsers, restricts web pages from accessing resources hosted on domains different from their own, preventing potential security vulnerabilities. CORS allows web applications to relax these restrictions selectively by specifying permissions through HTTP headers. When a web page makes a cross-origin request, the server hosting the resource must respond with appropriate CORS headers, notably the "Access-Control-Allow-Origin" header, which specifies which domains are allowed to access the resource. Additionally, headers like "Access-Control-Allow-Methods" and "Access-Control-Allow-Headers" define permitted HTTP methods and headers for the request. In some cases, for complex requests, the browser sends a preflight request to the server using the HTTP OPTIONS method to confirm the allowed methods and headers. Properly configuring CORS on the server side is essential for security, as overly permissive settings can expose your resources to potential security risks. CORS is a vital aspect of web development when dealing with cross-origin API requests and ensuring the security of web applications.
Example of CORS usage
Scenario: You have a website at https://www.mywebsite.com, and you want to fetch data from an API hosted at https://api.example.com.
Without CORS: If the API at https://api.example.com does not have CORS enabled, your web page at https://www.mywebsite.com won't be able to make requests to it due to the same-origin policy, resulting in a browser error.
With CORS Enabled: If the API at https://api.example.com has CORS enabled, and it includes the appropriate headers (e.g., Access-Control-Allow-Origin with https://www.mywebsite.com), your web page can make requests to the API, and the browser will allow it. This allows you to successfully fetch data from https://api.example.com and use it in your web application.
Conclusion
In conclusion, Cross-Origin Resource Sharing (CORS) is a security mechanism that allows web browsers to relax their same-origin policy selectively. By configuring appropriate HTTP headers on the server, CORS permits cross-origin requests, enabling web applications to fetch data and resources from different domains while maintaining security and control. This is crucial for building modern web applications that interact with various APIs and services.